In my previous article, I proposed the idea of creating a copilot developer experience that allows developers to work together on designing and building copilots, specifically when using generative AI and using company data sources for grounding. I also mentioned the documentation that I found, which had this statement: To share a bot with others in the environment, users must have the Environment maker security role.
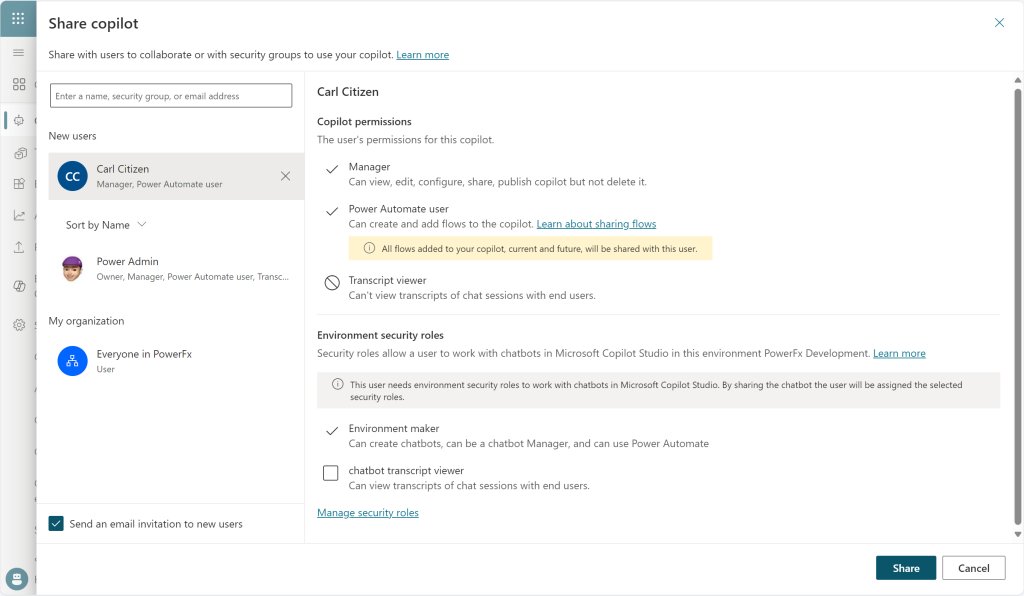
I wanted to test it in one of my development environments where my Power Admin (who has the Environment Maker and System Administrator roles) created a copilot. To collaborate with user Carl (who only has the Basic User role), I shared the copilot with him. However, since he doesn’t have enough environment permissions, the dialog above shows that the Environment maker role is automatically selected when sharing.
I wonder if there are other options besides assigning the Environment maker security role to all developers in an environment. This might be suitable for some developer collaboration scenarios, but it seems to violate the principle of least privilege. The Environment maker role grants access to 164 tables and 8 miscellaneous privileges. Are these all necessary for copilot development?

I created a custom security role and set the table permissions that a user would need to use this role. The visual above shows that my role only contains 65 tables and 5 miscellaneous privileges, which are not visible in the image. I assigned this role to one of my developers, Sanjay, in this environment. Here is the outcome.
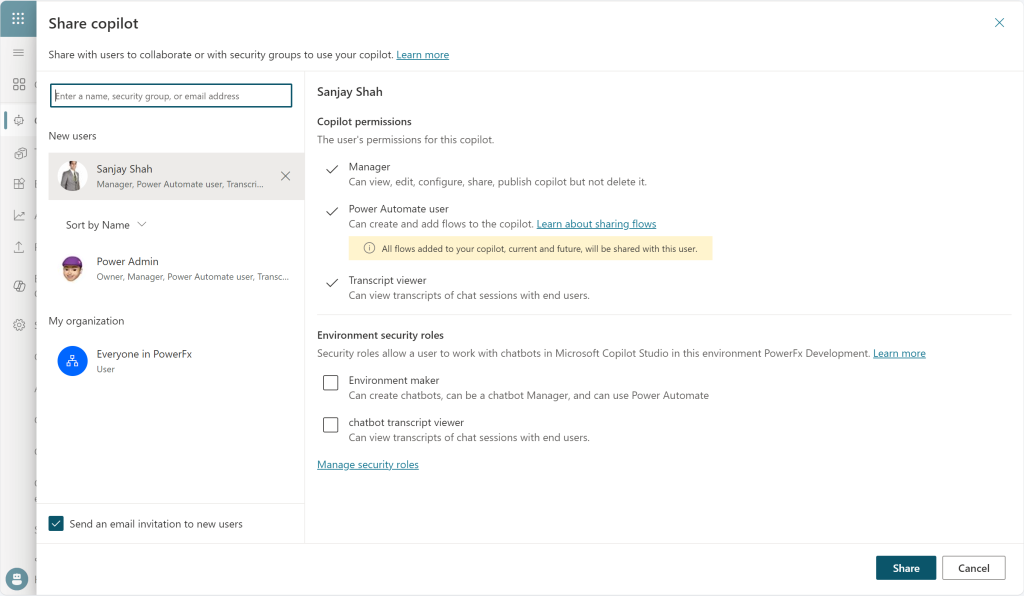
As you can see, the Environment maker security role is no longer pre-selected. So, I completed the sharing process and logged in as Sanjay to examine the outcome of sharing the copilot.

My user can interact and collaborate with the original copilot author seamlessly and enhance the copilot experience. This was a successful outcome of creating a custom security role and assigning this role to my developer before starting the sharing process. For daily use, I can now make sure that my copilot developers get the new security role automatically – for example, by creating a security group that assigns this role to every member.
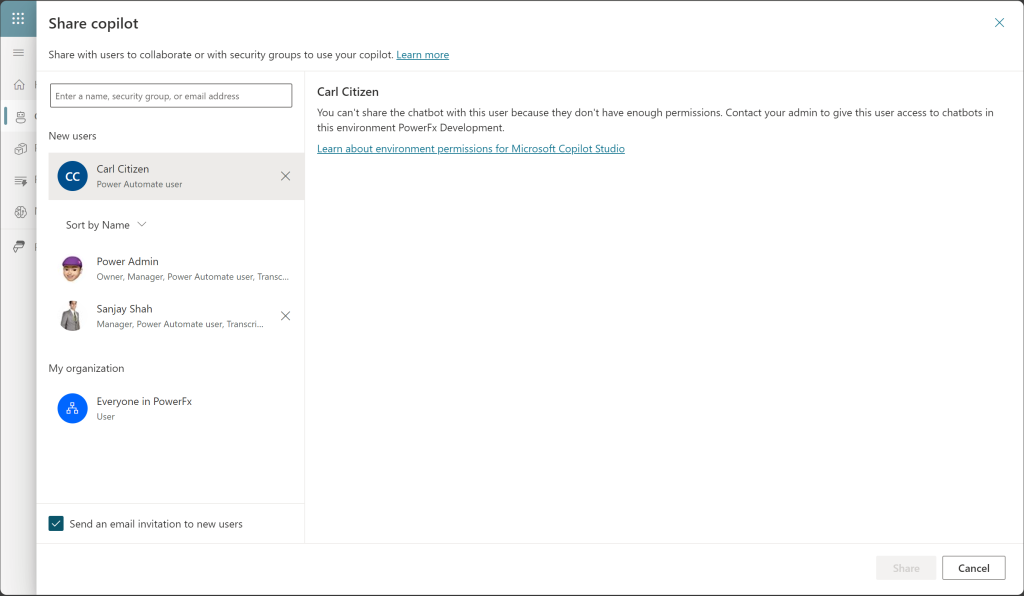
The final step was to test what happens when Sanjay shares the copilot with other users. The image above shows the outcome of his attempt to share it with Carl, who is not a developer in this environment and only has the Basic user role. This is an excellent result, because Sanjay does not have the permission to „promote“ Carl to an Environment maker. This way, I can ensure that I have control over the access level for my developer environment(s).
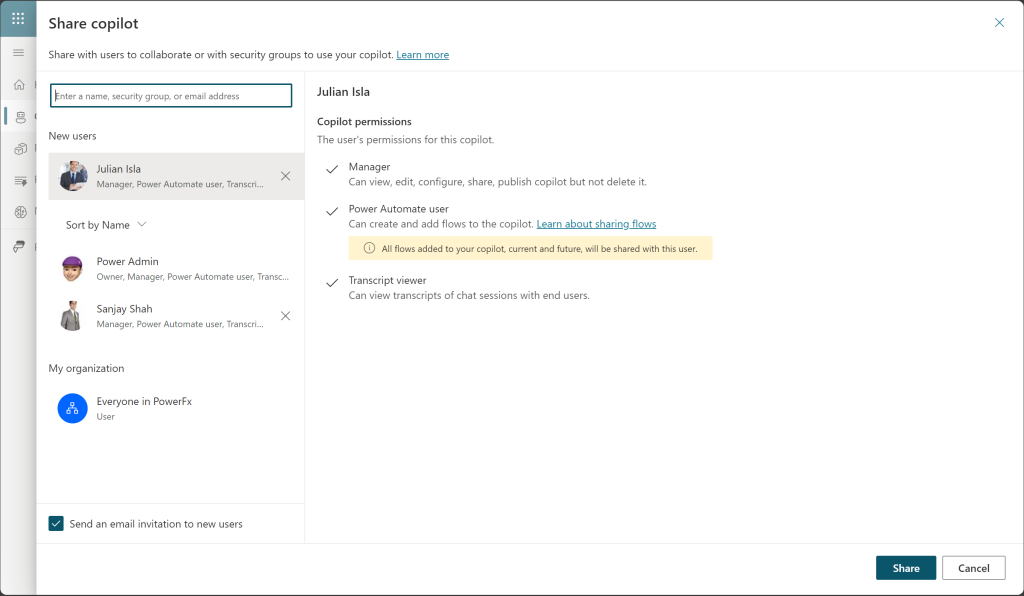
Suppose this project requires another developer and Julian needs to work on this copilot. The share dialog visual above shows the result of Sanjay sharing the copilot with Julian. Copilot permissions are already set, and there is no Environment security section to avoid unnecessary access. Julian can then interact and collaborate with the other copilot developers on this project.
This brief exercise demonstrates that it is sometimes valuable to understand the underlying mechanisms and explore the custom options to enhance the security of your Power Platform environments and to monitor the developers who are granted privileges. I hope this exercise encourages you to invest your time in a Power Platform environment strategy that includes the security role assignment process. I am confident that there is more to discover when we discuss using „Managed environment“ and features such as Environment groups. Until then,…
Update: As I received a lot of requests around how such custom security role could look like, please find my composed security role here.